Welcome to DU!
The truly grassroots left-of-center political community where regular people, not algorithms, drive the discussions and set the standards.
Join the community:
Create a free account
Support DU (and get rid of ads!):
Become a Star Member
Latest Breaking News
Editorials & Other Articles
General Discussion
The DU Lounge
All Forums
Issue Forums
Culture Forums
Alliance Forums
Region Forums
Support Forums
Help & Search
General Discussion
Related: Editorials & Other Articles, Issue Forums, Alliance Forums, Region ForumsYour USB cable, the spy: Inside the NSA’s catalog of surveillance magic
by Sean Gallagher
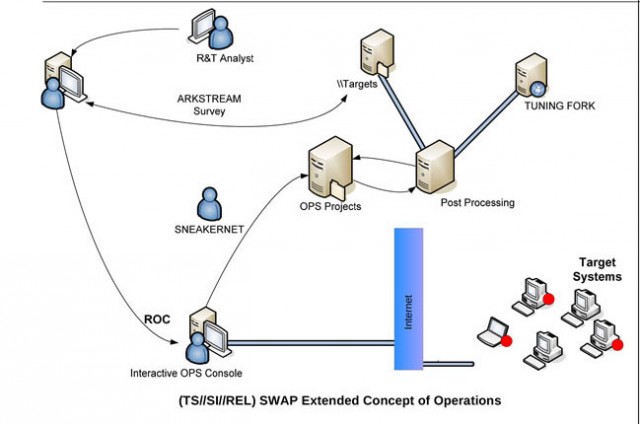
A diagram of an NSA BIOS-based attack, brought to you by sneakernet.
The National Security Agency’s sophisticated hacking operations go way beyond using software vulnerabilities to gain access to targeted systems. The agency has a catalog of tools available that would make James Bond’s Q jealous, providing NSA analysts access to just about every potential source of data about a target.
In some cases, the NSA has modified the firmware of computers and network hardware—including systems shipped by Cisco, Dell, Hewlett-Packard, Huawei, and Juniper Networks—to give its operators both eyes and ears inside the offices the agency has targeted. In others, the NSA has crafted custom BIOS exploits that can survive even the reinstallation of operating systems. And in still others, the NSA has built and deployed its own USB cables at target locations—complete with spy hardware and radio transceiver packed inside.
Documents provided by former NSA contractor Edward Snowden to Der Spiegel reveal a fantastical collection of surveillance tools dating back to 2007 and 2008 that gave the NSA the power to collect all sorts of data over long periods of time without detection. The tools, ranging from back doors installed in computer network firmware and software to passively powered bugs installed within equipment, give the NSA a persistent ability to monitor some targets with little risk of detection. While the systems targeted by some of the “products” listed in the documents are over five years old and are likely to have been replaced in some cases, the methods and technologies used by all the exploit products could easily still be in use in some form in ongoing NSA surveillance operations.
more
http://arstechnica.com/information-technology/2013/12/inside-the-nsas-leaked-catalog-of-surveillance-magic/
2 replies
 = new reply since forum marked as read
Highlight:
NoneDon't highlight anything
5 newestHighlight 5 most recent replies
= new reply since forum marked as read
Highlight:
NoneDon't highlight anything
5 newestHighlight 5 most recent replies
Your USB cable, the spy: Inside the NSA’s catalog of surveillance magic (Original Post)
n2doc
Dec 2013
OP
snooper2
(30,151 posts)1. LOL, the NSA got Huawei to modify their hardware for surveillance
Can't wait till our Juniper dude is back on Thursday
friendly_iconoclast
(15,333 posts)2. The catalog, in photo form: