Researchers Solve Juniper Backdoor Mystery; Signs Point to NSA
Source: Wired
Security researchers believe they have finally solved the mystery around how a sophisticated backdoor embedded in Juniper firewalls works. Juniper Networks, a tech giant that produces networking equipment used by an array of corporate and government systems, announced on Thursday that it had discovered two unauthorized backdoors in its firewalls, including one that allows the attackers to decrypt protected traffic passing through Juniper’s devices.
The researchers’ findings suggest that the NSA may be responsible for that backdoor, at least indirectly. Even if the NSA did not plant the backdoor in the company’s source code, the spy agency may in fact be indirectly responsible for it by having created weaknesses the attackers exploited.
Evidence uncovered by Ralf-Philipp Weinmann, founder and CEO of Comsecuris, a security consultancy in Germany, suggests that the Juniper culprits repurposed an encryption backdoor previously believed to have been engineered by the NSA, and tweaked it to use for their own spying purposes. Weinmann reported his findings in an extensive post published late Monday.
They did this by exploiting weaknesses the NSA allegedly placed in a government-approved encryption algorithm known as Dual_EC, a pseudo-random number generator that Juniper uses to encrypt traffic passing through the VPN in its NetScreen firewalls. But in addition to these inherent weaknesses, the attackers also relied on a mistake Juniper apparently made in configuring the VPN encryption scheme in its NetScreen devices, according to Weinmann and other cryptographers who examined the issue. This made it possible for the culprits to pull off their attack.
Read more: http://www.wired.com/2015/12/researchers-solve-the-juniper-mystery-and-they-say-its-partially-the-nsas-fault/
Weinmann's post:
http://rpw.sh/blog/2015/12/21/the-backdoored-backdoor/
The NSA backdoor is known as FEEDTROUGH:
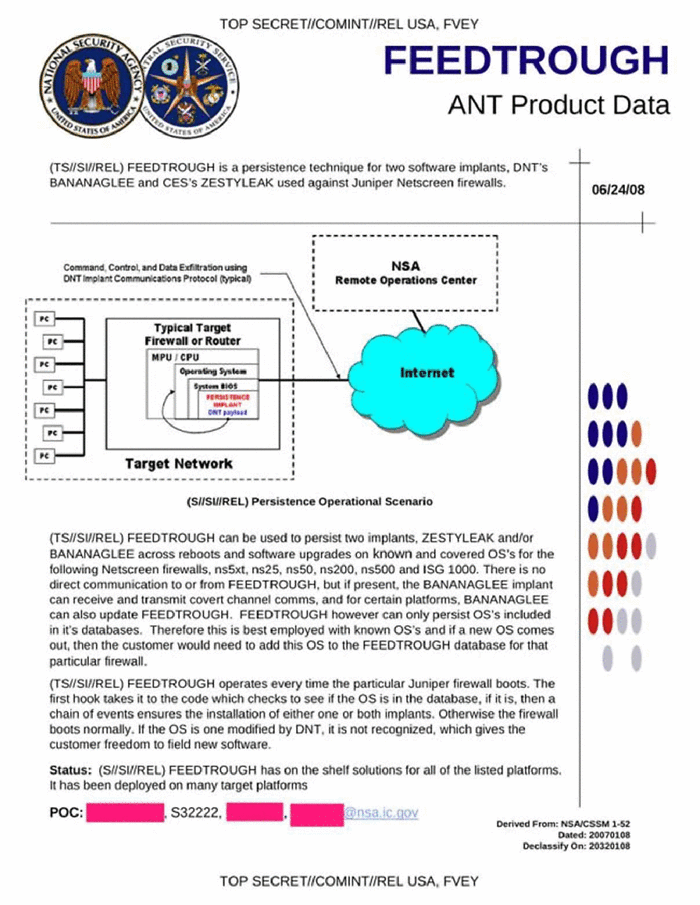
Ichingcarpenter
(36,988 posts)US should be able to bypass encryption—but only for terrorists, candidate says.
Presidential candidate Hillary Clinton has called for a "Manhattan-like project" to help law enforcement break into encrypted communications. This is in reference to the Manhattan Project, the top-secret concentrated research effort which resulted in the US developing nuclear weapons during World War II.
At Saturday's Democratic debate (transcript here), moderator Martha Raddatz asked Clinton about Apple CEO Tim Cook's statements that any effort to break encryption would harm law-abiding citizens.
"You've talked a lot about bringing tech leaders and government officials together, but Apple CEO Tim Cook said removing encryption tools from our products altogether would only hurt law-abiding citizens who rely on us to protect their data," Raddatz said. "So would you force him to give law enforcement a key to encrypted technology by making it law?"
Clinton said she "would not want to go to that point" of forcing companies like Apple to give encryption keys to law enforcement.
"I would hope that, given the extraordinary capacities that the tech community has and the legitimate needs and questions from law enforcement, that there could be a Manhattan-like project, something that would bring the government and the tech communities together to see they're not adversaries, they've got to be partners,"
Though Clinton said she has "confidence in our tech experts" to solve this problem, she has continued pushing for weakening encryption despite warnings from Apple, Google, Microsoft, and other tech companies that putting encryption back doors into their products would weaken data security for everyone.
Cook discussed encryption further last night on 60 Minutes. The Apple CEO explained encryption back doors would help anyone—not just law enforcement—access people's private information.
"On your smartphone today, on your iPhone, there's likely health information, there's financial information," Cook said. "There are intimate conversations with your family, or your co-workers. There's probably business secrets and you should have the ability to protect it. And the only way we know how to do that, is to encrypt it. Why is that? It's because if there's a way to get in, then somebody will find the way in. There have been people that suggest that we should have a back door. But the reality is if you put a back door in, that back door's for everybody, for good guys and bad guys."
http://arstechnica.com/tech-policy/2015/12/hillary-clinton-wants-manhattan-like-project-to-break-encryption/
Clinton's Big Brotherish proposal at Saturday's Democratic debate was both troubling and vague
You might imagine that Clinton — of all people — would be sensitive to the liberty interests of hiding personal communications from prying eyes. This is the public servant, after all, who as secretary of state maintained a private email server — with the benefit to Clinton of being able to vet and delete her own communications before they became a permanent part of the public record.
In this context, it was troubling Saturday evening to hear Clinton's response to a question about the power of high technology to ensure privacy. Blasting "encrypted communication that no law enforcement agency can break into," Clinton said, "I would hope that, given the extraordinary capacities that the tech community has and the legitimate needs and questions from law enforcement, that there could be a Manhattan-like project — something that would bring the government and the tech communities together to see they're not adversaries, they've got to be partners."
The reaction from America's most famous privacy whistleblower was swift:
Edward Snowden ✔ @Snowden
Aaaaaaaaand Hillary just terrified everyone with an internet connection. #DemDebate
3:07 AM - 20 Dec 2015
Read more: http://www.rollingstone.com/politics/news/edward-snowden-clintons-call-for-a-manhattan-like-project-is-terrifying-20151220#ixzz3uyvrxGFl
Pholus
(4,062 posts)Thanks NSA!
jberryhill
(62,444 posts)Nihil
(13,508 posts)Don't want something like this to sink into quiet obscurity ...
IthinkThereforeIAM
(3,292 posts)... Wall Street loves insider info, corporate statements, the proverbial early data on FCOJ (Trading Places), emails, etc...$$$
Downwinder
(12,869 posts)would that mean that all VPN is compromised?
PosterChild
(1,307 posts).... a VPN is used to "tunnel" through unsecure networks into a network that is internally secure . It is not generally used to connect one VPN to another in a peer-to-peer arrangement. So compatibility with other VPNs is not generally needed.
Downwinder
(12,869 posts)hunter
(40,476 posts)Blue_Tires
(57,596 posts)Last edited Tue Dec 22, 2015, 12:15 PM - Edit history (1)
and let their own hackers exploit it...
 :large
:large
hunter
(40,476 posts)Wanna see someone with a really creepy porn collection?
That's a spy.
PosterChild
(1,307 posts)..... law enforcement capability. The constitution provides for reasonable search and seizure. There is a large body of law governing what is and isn't reasonable.
What is the problem with that?
Response to friendly_iconoclast (Original post)
Name removed Message auto-removed
PosterChild
(1,307 posts).... of a compromise is that an encryption parameter was changed and then changed back to its original value. There is no evidence that this was done delibertly, that the altered value was weak, or that the original value is weak. No evidence that anyone did or attempted to exploit the hypothetical weakness .
Seems like a lot of speculation to me.
Ichingcarpenter
(36,988 posts)Your expertise, education, research, heading your own security company?
PosterChild
(1,307 posts)... just noted the weakness of the evidence given in the referenced article.
I do work in an organization that seriously investigates these issues - i don't do so but I'm more exposed to infomation concerning them than others might be.
Ichingcarpenter
(36,988 posts)Ralf-Philipp Weinmann
Director, Comsecuris UG (haftungsbeschränkt)
Binary Analysis, Reverse Engineering, Mobile/Embedded/Wireless Security, Cryptology
Breaking 104 bit WEP in less than 60 seconds
E Tews, RP Weinmann, A Pyshkin
Information Security Applications, 188-202 225 2007
MutantXL
J Ding, J Buchmann, MSE Mohamed, WSAE Mohamed, RP Weinmann
64 2008
Analysis of the SMS4 block cipher
F Liu, W Ji, L Hu, J Ding, S Lv, A Pyshkin, RP Weinmann
Information Security and Privacy, 158-170 60 2007
Trawling for tor hidden services: Detection, measurement, deanonymization
A Biryukov, I Pustogarov, R Weinmann
Security and Privacy (SP), 2013 IEEE Symposium on, 80-94 46 2013
Block ciphers sensitive to Gröbner basis attacks
J Buchmann, A Pyshkin, RP Weinmann
Topics in Cryptology–CT-RSA 2006, 313-331 41 2006
A Framework for Automated Architecture-Independent Gadget Search.
T Dullien, T Kornau, RP Weinmann
WOOT 40 2010
iOS Hacker's Handbook
C Miller, D Blazakis, D DaiZovi, S Esser, V Iozzo, RP Weinmann
John Wiley & Sons 36 2012
A zero-dimensional Gröbner basis for AES-128
J Buchmann, A Pyshkin, RP Weinmann
Fast Software Encryption, 78-88 35 2006
Analysis of the DVB common scrambling algorithm
RP Weinmann, K Wirt
Communications and Multimedia Security, 195-207 34 2005
Attacks on the DECT authentication mechanisms
S Lucks, A Schuler, E Tews, RP Weinmann, M Wenzel
Topics in Cryptology–CT-RSA 2009, 48-65 23 2009
Meet-in-the-middle attacks on SHA-3 candidates
D Khovratovich, I Nikolić, RP Weinmann
Fast Software Encryption, 228-245 21 2009
Practical cryptanalysis of ISO/IEC 9796-2 and EMV signatures
JS Coron, D Naccache, M Tibouchi, RP Weinmann
Advances in Cryptology-CRYPTO 2009, 428-444 20 2009
Post-Quantum Signatures.
J Buchmann, LCC García, M Döring, D Engelbert, C Ludwig, R Overbeck, ...
IACR Cryptology ePrint Archive 2004, 297 20 2004
Cryptanalysis of the DECT standard cipher
K Nohl, E Tews, RP Weinmann
Fast Software Encryption, 1-18 19 2010
Baseband Attacks: Remote Exploitation of Memory Corruptions in Cellular Protocol Stacks.
RP Weinmann
WOOT, 12-21 18 2012
All Your Baseband Are Belong To Us
RP Weinmann
hack. lu 13 2010
Evaluating algebraic attacks on the AES
RP Weinmann
Diplom thesis, Technische Universität Darmstadt 13 2003
Block ciphers: algebraic cryptanalysis and Groebner bases
C Cid, RP Weinmann
Groebner bases, coding, and cryptography, 307-327 12 2009
TorScan: Tracing long-lived connections and differential scanning attacks
A Biryukov, I Pustogarov, RP Weinmann
Computer Security–ESORICS 2012, 469-486 8 2012
An efficient FPGA implementation for an DECT brute-force attacking scenario
HG Molter, K Ogata, E Tews, RP Weinmann
Wireless and Mobile Communications, 2009. ICWMC'09. Fifth International ... 8 2009
That was page one .... there are more pages
https://scholar.google.dk/citations?user=1JxJ1AIAAAAJ&hl=da&cstart=20&pagesize=20
I think I'll listen to this guy vs......... I know someone who knows someone
PosterChild
(1,307 posts)Last edited Tue Dec 22, 2015, 11:04 PM - Edit history (1)
... and there is no doubt that ecliptic curve random number generation is compromised if you don't select the right parameters, and that the default parameters that come with the standard library are weak, and that NSA lobbied NIST to adopt the library as standard.
It's also true that if you do select the proper parameters it's secure.
The article states that the original parameter was delibertly selected by juniper to be secure. It states that the parameter was changed to a value which is not known to be either secure or compromised. And that when the change was discovered in a code review it was changed back to the uncompromised value.
At this time no evidence has been given to show that the change was deliberate, let alone done by an attacker, let alone a state sponsored attacker, let alone the NSA. Nor did anyone say that the changed value was ever compromised .
Since the FBI is investigating, we might get some answers.
joshcryer
(62,536 posts)It's just one of those agencies that exists to exist but does nothing useful.
Ichingcarpenter
(36,988 posts)BTW........ what does it really mean.''that the NSA simply isn't doing its job.''?
PosterChild
(1,307 posts)... not providing patches for openSSL.
They are very good at what they do. Very, very good.
Pholus
(4,062 posts)As is CLEARLY stated in their mission statement.
https://www.nsa.gov/about/index.shtml
Of course, it gets confusing when early in W's administration they started volunteering stuff like this:
http://linux.slashdot.org/story/00/12/22/0157229/nsa-releases-high-security-version-of-linux
But of course we now know it was always about getting as many U.S. computers and firewalls compromised as possible. Like this:
http://www.securityweek.com/nsa-gchq-linked-efforts-compromise-antivirus-vendors-report
Thanks NSA! For jack and squat. They're just as bad as the Russian cybercriminals when it comes to caring about individual citizens.
PosterChild
(1,307 posts)I don't think it is NSA s resposibility to provide patches for openSSL . That just isn't their job.
PosterChild
(1,307 posts)... which links to the intercept which states:
I don't see any thing wrong with this. In order to collect signals intelligence on foreign computing sources they have to defeat, overcome and exploit protections that have been installed on them.
This is what they are supposed to be doing. I'm in support of it.
PosterChild
(1,307 posts).... their information assurance responsibility...
Believe me, the openSSL heartbleed defect did not in any way compromise any classified information. Mission accomplished.
Pholus
(4,062 posts)hahahaha
PosterChild
(1,307 posts)....explain a bit more fully,
PosterChild
(1,307 posts).... funded by DARPA. DARPA went to the right folks.
Linux is notoriously skimpy on security , but it's a good environment for a lot of projects. This program seems like a good idea to me.
JonLeibowitz
(6,282 posts)PosterChild
(1,307 posts)
If they attack we will fight to the end
benld74
(10,271 posts)Years ago. I had never heard of Junioer before that.
Blue_Tires
(57,596 posts)friendly_iconoclast
(15,333 posts)And all because Juniper had already paved the road.
So why does this matter?
For the past several months I've been running around with various groups of technologists, doing everything I can to convince important people that the sky is falling. Or rather, that the sky will fall if they act on some of the very bad, terrible ideas that are currently bouncing around Washington -- namely, that our encryption systems should come equipped with "backdoors" intended to allow law enforcement and national security agencies to access our communications.
One of the most serious concerns we raise during these meetings is the possibility that encryption backdoors could be subverted. Specifically, that a backdoor intended for law enforcement could somehow become a backdoor for people who we don't trust to read our messages. Normally when we talk about this, we're concerned about failures in storage of things like escrow keys. What this Juniper vulnerability illustrates is that the danger is much broader and more serious than that.
Octafish
(55,745 posts)PROsecution Management Information System software used to track "individuals" and their cases as they routed through the criminal justice system was modified in the mid-80s, for profit, by friends of Ed Meese II, Ronald Reagan and George H.W. Bush. Small world.
http://www.wired.com/1993/01/inslaw/
Case proves BFEE is above the law.
