Hissyspit
Hissyspit's JournalNSA Whistleblower William Binney: "FBI came in and pointed a gun at me" (2007)
22nd August 2012 NYT Op Docs
The filmmaker Laura Poitras profiles William Binney, a 32-year veteran of the National Security Agency who helped design a top-secret program he says is broadly collecting Americans' personal data.
This video is part of a series by independent filmmakers who have received grants from the BRITDOC Foundation and the Sundance Institute.
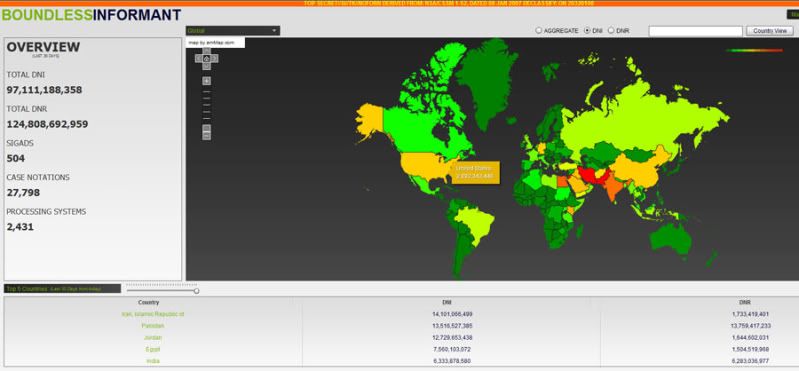
Boundless Informant: The NSA's Secret Tool to Track Global Surveillance Data
Source: The Guardian
Boundless Informant: the NSA's secret tool to track global surveillance data
Revealed: The NSA's powerful tool for cataloging data – including figures on US collection
Glenn Greenwald and Ewen MacAskill
guardian.co.uk, Saturday 8 June 2013 15.10 EDT
The National Security Agency has developed a powerful tool for recording and analysing where its intelligence comes from, raising questions about its repeated assurances to Congress that it cannot keep track of all the surveillance it performs on American communications.
The Guardian has acquired top-secret documents about the NSA datamining tool, called Boundless Informant, that details and even maps by country the voluminous amount of information it collects from computer and telephone networks.
The focus of the internal NSA tool is on counting and categorizing the records of communications, known as metadata, rather than the content of an email or instant message.
The Boundless Informant documents show the agency collecting almost 3 billion pieces of intelligence from US computer networks over a 30-day period ending in March 2013. One document says it is designed to give NSA officials answers to questions like, "What type of coverage do we have on country X" in "near real-time by asking the SIGINT [signals intelligence] infrastructure."
- snip -
A snapshot of the Boundless Informant data, contained in a top secret NSA "global heat map" seen by the Guardian, shows that in March 2013 the agency collected 97bn pieces of intelligence from computer networks worldwide.
Read more: http://www.guardian.co.uk/world/2013/jun/08/nsa-boundless-informant-global-datamining
Guardian: New Alleged PRISM Slide Released "Collection Directly From the Servers"
http://www.guardiannews.com/world/2013/jun/08/nsa-surveillance-prism-obama-liveLIVE Saturday 8 June 2013 13.30 EDT
NSA Prism program: more details revealed in new slide – live updates
Google and Facebook issue strong denials of participation in Prism as Obama meets with Chinese counterpart
Tom McCarthy
8 min ago
New Prism slide
- snip -
While many of these have provided useful insight and detail into the operation of the program, several of the reports do not tally with the information obtained by the Guardian.
Some articles have claimed that Prism is not a tool used for the collection of information from US companies, but is instead an internal tool used to analyse such information.
Others have speculated – in the light of denials from technology companies about granting "direct access" to servers – that Prism operates through interception of communication cables.
Both of these theories appear to be contradicted by internal NSA documents.
In the interests of aiding the debate over how Prism works, the Guardian is publishing an additional slide from the 41-slide presentation which details Prism and its operation. We have redacted some program names.
The slide, below, details different methods of data collection under the FISA Amendment Act of 2008 (which was renewed in December 2012). It clearly distinguishes Prism, which involves data collection from servers, as distinct from four different programs involving data collection from "fiber cables and infrastructure as data flows past".
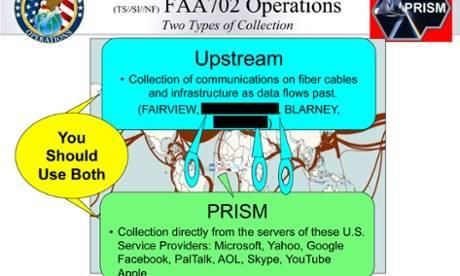
A slide from the NSA Prism presentation that gives more details of the secretive program. Photograph: /Guardian
- snip -
The Guardian's initial reporting of Prism made clear the technology companies denied all knowledge of the program, and did not speculate on whether it would need such co-operation in order to work.
MORE AT LINK
Obama Orders US to Draw Up Overseas Target List for Cyber-Attacks
Source: Guardian (UK) / Glenn Greenwald and Ewen McAskill
Obama orders US to draw up overseas target list for cyber-attacks
Exclusive: Top-secret directive steps up offensive cyber capabilities to 'advance US objectives around the world'
• Read the secret presidential directive here: http://www.guardian.co.uk/world/interactive/2013/jun/07/obama-cyber-directive-full-text
Glenn Greenwald and Ewen MacAskill
guardian.co.uk, Friday 7 June 2013 15.06 EDT
Barack Obama has ordered his senior national security and intelligence officials to draw up a list of potential overseas targets for US cyber-attacks, a top secret presidential directive obtained by the Guardian reveals.
The 18-page Presidential Policy Directive 20, issued in October last year but never published, states that what it calls Offensive Cyber Effects Operations (OCEO) "can offer unique and unconventional capabilities to advance US national objectives around the world with little or no warning to the adversary or target and with potential effects ranging from subtle to severely damaging".
- snip -
The directive also contemplates the possible use of cyber actions inside the US, though it specifies that no such domestic operations can be conducted without the prior order of the president, except in cases of emergency.
The aim of the document was "to put in place tools and a framework to enable government to make decisions" on cyber actions, a senior administration official told the Guardian.
The administration published some declassified talking points from the directive in January 2013, but those did not mention the stepping up of America's offensive capability and the drawing up of a target list.
Read more: http://www.guardian.co.uk/world/2013/jun/07/obama-china-targets-cyber-overseas
NSA Spying: Whistleblowers Claim Vindication On Surveillance State Warnings
http://www.huffingtonpost.com/2013/06/06/nsa-spying-whistleblowers_n_3399258.htmlGerry Smith
Ryan J. Reilly
NSA Spying: Whistleblowers Claim Vindication On Surveillance State Warnings
Posted: 06/06/2013 8:30 pm EDT | Updated: 06/06/2013 9:19 pm EDT
For years, four former National Security Agency analysts warned that the government was conducting widespread surveillance on domestic communications. Their warnings were largely ignored.
- snip -
While at the NSA, Wiebe, along with Ed Loomis and Bill Binney, created a computer program that could isolate large amounts of information collected by the NSA while protecting Americans’ privacy. But the NSA ignored their program, saying “it was too invasive,” Loomis said.
"We had a solution to this entire problem that would have avoided this whole mess," Wiebe said.
Instead, the NSA chose Trailblazer, a multi-billion dollar computer program that was supposed to revolutionize how the agency analyzed communications data. Wiebe, Loomis and Binney called for an investigation into Trailblazer, citing massive waste and fraud.
In response, Binney and Wiebe were accused of leaking classified information to the press. The FBI raided their homes. Still, they continued to speak publicly about their concerns about the NSA invading Americans' privacy.
- snip -
“This would appear to be the hardcore evidence that I think a lot of people needed to start to believe it,” Binney, who was at the NSA for nearly 40 years, told The Huffington Post. “It’s domestic spying, that’s what it is, on a very large scale.”
A fourth NSA whistleblower, Thomas Drake, criticized the court that authorized the surveillance.
- snip -
“Why do you need to trample on the Constitution for this crazy war on terror?” Loomis said.
MORE[p]
Who Was The Only U.S. Senator to Vote Against The "PATRIOT" Act in 2001?
Answer found HERE.
Did you get it?
Breaking: Intelligence Chief Declassifies (Some) Phone Data Program Details
Source: Associated Press
https://twitter.com/AP/status/342831134591299585
The Associated PressVerified account
?@AP
BREAKING: Intelligence chief declassifies phone data program details, says public must understand limits
INTELLIGENCE CHIEF BLASTS NSA DOCUMENT LEAKS
By JOSH LEDERMAN
— Jun. 6 10:49 PM EDT
WASHINGTON (AP) — The director of national intelligence is trying to set the record straight after leaked documents revealed information about two top-secret intelligence-gathering programs.
James Clapper says the disclosure of an Internet surveillance program is "reprehensible" and a document leak about a phone records program could cause long-lasting and irreversible harm to the nation's ability to respond to threats.
Clapper says articles about the programs contained inaccuracies and omitted key information. He's declassifying some details about the authority used in the phone records program because he says Americans must know the program's limits.
Those details include that a special court reviews the program every 90 days. He says the court prohibits the government from indiscriminately sifting through phone data and queries are only allowed when facts support reasonable suspicion.
Read more: http://bigstory.ap.org/article/intelligence-chief-blasts-nsa-document-leaks
http://www.dni.gov/index.php/newsroom/press-releases/191-press-releases-2013/869-dni-statement-on-activities-authorized-under-section-702-of-fisa
DNI Statement on Activities Authorized Under Section 702 of FISA
Thursday, June 06, 2013
June 6, 2013
DNI Statement on Activities Authorized Under Section 702 of FISA
The Guardian and The Washington Post articles refer to collection of communications pursuant to Section 702 of the Foreign Intelligence Surveillance Act. They contain numerous inaccuracies.
Section 702 is a provision of FISA that is designed to facilitate the acquisition of foreign intelligence information concerning non-U.S. persons located outside the United States. It cannot be used to intentionally target any U.S. citizen, any other U.S. person, or anyone located within the United States.
Activities authorized by Section 702 are subject to oversight by the Foreign Intelligence Surveillance Court, the Executive Branch, and Congress. They involve extensive procedures, specifically approved by the court, to ensure that only non-U.S. persons outside the U.S. are targeted, and that minimize the acquisition, retention and dissemination of incidentally acquired information about U.S. persons.
Section 702 was recently reauthorized by Congress after extensive hearings and debate.
Information collected under this program is among the most important and valuable foreign intelligence information we collect, and is used to protect our nation from a wide variety of threats.
The unauthorized disclosure of information about this important and entirely legal program is reprehensible and risks important protections for the security of Americans.
James R. Clapper, Director of National Intelligence
U.S. Intelligence Mining Data from Nine U.S. Internet Companies in Broad Secret Program
Source: Washington Post
U.S. intelligence mining data from nine U.S. Internet companies in broad secret program
By Barton Gellman and Laura Poitras, Published: THURSDAY, JUNE 06, 5:43 PM ET
The National Security Agency and the FBI are tapping directly into the central servers of nine leading U.S. Internet companies, extracting audio, video, photographs, e-mails, documents and connection logs that enable analysts to track a person’s movements and contacts over time.
The highly classified program, code-named PRISM, has not been disclosed publicly before. Its establishment in 2007 and six years of exponential growth took place beneath the surface of a roiling debate over the boundaries of surveillance and privacy. Even late last year, when critics of the foreign intelligence statute argued for changes, the only members of Congress who know about PRISM were bound by oaths of office to hold their tongues.
An internal presentation on the Silicon Valley operation, intended for senior analysts in the NSA’s Signals Intelligence Directorate, described the new tool as the most prolific contributor to the President’s Daily Brief, which cited PRISM data in 1,477 articles last year. According to the briefing slides, obtained by The Washington Post, “NSA reporting increasingly relies on PRISM” as its leading source of raw material, accounting for nearly 1 in 7 intelligence reports.
That is a remarkable figure in an agency that measures annual intake in the trillions of communications. It is all the more striking because the NSA, whose lawful mission is foreign intelligence, is reaching deep inside the machinery of American companies that host hundreds of millions of American-held accounts on American soil.
The technology companies, which participate knowingly in PRISM operations, include most of the dominant global players of Silicon Valley. They are listed on a roster that bears their logos in order of entry into the program: “Microsoft, Yahoo, Google, Facebook, PalTalk, AOL, Skype, YouTube, Apple.” PalTalk, although much smaller, has hosted significant traffic during the Arab Spring and in the ongoing Syrian civil war.
Read more: http://www.washingtonpost.com/investigations/us-intelligence-mining-data-from-nine-us-internet-companies-in-broad-secret-program/2013/06/06/3a0c0da8-cebf-11e2-8845-d970ccb04497_story.html
Reuters: Senior Obama Official Acknowledges Collection of Information; Will Be Leak Probe
UPDATE: Reuters: Senior Obama administration official acknowledges collection of information on Verizon calls. NBC: White House today won't confirm facts but defends practice. NBC's Pete Williams reports he was told "definitely there will be a leak investigation."
http://gregmitchellwriter.blogspot.com/2013/06/orwellian.html
Al Gore Calls Obama Administration’s Collection of Phone Records ‘Obscenely Outrageous’
Source: Washington Post
Al Gore calls Obama administration’s collection of phone records ‘obscenely outrageous’
By Aaron Blake, Published: JUNE 05, 10:39 PM ET
Former Democratic presidential candidate Al Gore on Wednesday night leveled some rare and harsh criticism at the Obama administration, attacking its reported collection of phone records for millions of Americans.
The Guardian’s Glenn Greenwald reported Wednesday evening that the National Security Agency has used a secret court order issued in April to collect the records of all phone calls made on the Verizon network.
Gore took to Twitter to call the monitoring “obscenely outrageous.”
-- Al Gore (@algore) June 6, 2013
- snip -
The order reportedly allows the government to collect phone records for any of Verizon’s customers, even if they aren’t suspected of wrongdoing. It does not allow them to listen to the phone calls themselves.
Read more: http://www.washingtonpost.com/blogs/post-politics/wp/2013/06/05/al-gore-calls-obama-administrations-collection-of-phone-records-obscenely-outrageous/
Profile Information
Member since: Fri Nov 12, 2004, 08:39 AMNumber of posts: 45,788